Over the last few years, mobile technology has accelerated its growth and seen a massive increase in user base. Mobile applications store and process a wide variety of sensitive data, from credit card information to intellectual property to medical records. Malicious attackers easily target this sensitive information. According to research, there are nearly 20 million active vulnerabilities on mobile devices! Due to the blurring of the lines between secure and exposed data. Mobile Application Security Testing evaluates an application's security and a large pool of mobile application threat vectors to identify inherent vulnerabilities and ensure the application's secure state while in use.
In a black box penetration test, no information is provided to the tester at all. The pentester in this instance follows the approach of an unprivileged attacker, from initial access and execution through to exploitation. This scenario can be seen as the most realistic, proving how an adversary with no inside knowledge would target and compromise an organization. However, due to the extended amount of time required to research the target, black box test is one of the costly options available.
White box penetration testing involves sharing full network and system information with the tester, including network maps and credentials. A white box penetration test is useful for simulating a targeted attack on a specific system utilizing as many attack vectors as possible. Usually this type of a test is helpful at the time of product development to uncover required fixes.
Grey box tests strike a balance between depth and efficiency and can be used to simulate either an insider threat or an attack that has breached the network perimeter. In a grey box penetration test, only limited information is shared with the tester such as unprivileged login credentials and/or IP address of the target. Grey box testing is often favored by customers as the best balance between efficiency and authenticity, stripping out potentially time-consuming reconnaissance.
Know our process and Possimus delectus ex, harum, quis rerum maxime in magnam. lorem ipsum dolor sit amet, consectetur adipisicing elit.
Our Cyber Security professionals gain an understanding of the IT landscape and scope of work in an organisation during this phase. We conduct an assessment of the environment and compile data such as network architecture, application architecture, and other IT infrastructure-related data. For end-to-end testing and remediation of projects, we give a project plan with time and effort estimates. We go on to the next level after receiving approval and authorization from management.
The in-scope IT landscape is tested at this phase. We perform both manual and automated testing here.
Assess all results for severity, impact, and ease of exploitation, and assign risk ratings of High, Medium, or Low, along with explanations, proof-of-concepts, and remedial recommendations are processed in this phase. We run a revalidation test for detecting issues following the organization's remedies.
By performing static and dynamic testing on these applications, we assess all parts of the mobile application and launch attacks against those features to see if they would cause any security failures.
During a Mobile App Security Assessment, mobile app security experts use a rigorous methodology to determine the overall security posture of a given application. These experts model the threat posed by a range of threat actors with varying levels of sophistication. They'll be able to determine how resistant your mobile app is to these various threat. When security flaws are discovered, you'll be informed of the implications and, more importantly, how to resolve the issue. An in-depth mobile application security assessment will notify you of any identified positive security controls, allowing you to continue doing what you're doing with the confidence that you're doing things correctly.
No other Pentest product combines automated scanning + expert guidance like we do.
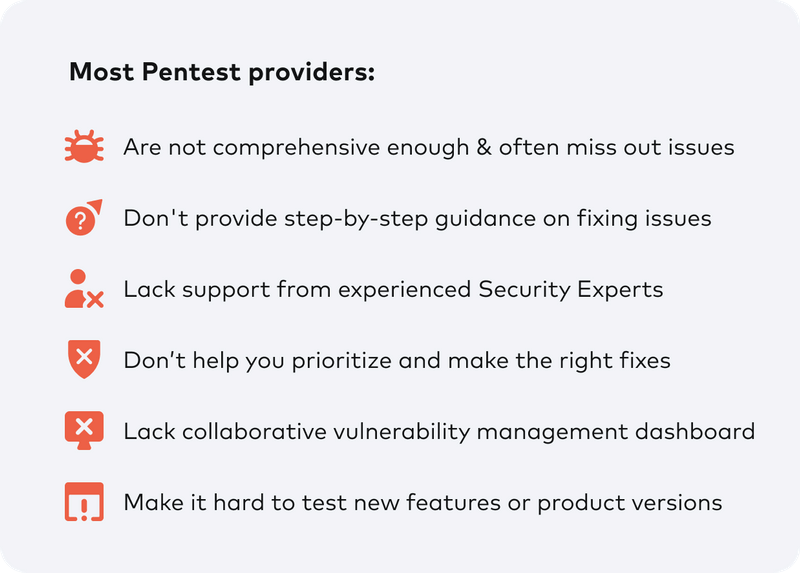
Everyone wants to make their own business the most secure and trustworthy brand for their customers.
Getting a pentest done to find and fix all the loopholes in your business is the next obvious step.
But the wrong Pentest partner could cost you months of progress and the reputation you’ve worked so hard to build.
LYFAUX Security is committed to providing businesses worldwide with cutting-edge cybersecurity solutions, and we are experts in our field. LYFAUX leverages the experience of a diverse team to provide services for a variety of technologies and complex web applications, resulting in the highest possible level of assurance.
Connect